The Magical Code Injection Rainbow (MCIR) a Web-based training projects
Dan Crowley, a data security aficionado and independent resheacher with Trustwave, has composed and brought forth five exceptionally amazing training suites. His Web-based training projects are easy to explore and come with different testing levels. His most recent creation is a pound up of his web mentors crushed into one advanced play area called, the Magical Code
Injection Rainbow (MCIR). MCIR is included the accompanying modules:
- SQLol – a SQL injection preparing stage that takes into account customization of white and listed characters and successions focused on a test based stage to prepare the fundamental skills important to test and defeat SQL efforts to establish safety.
- XMLmao – Like Sqlol, Xmlmao is a configurable XML injection training environment.
- Shelol – A configurable operating System shell training environment for command injection.
- XSSmh – Cross site scripting training tool.
- CryptOMG – CryptOMG is a configurable catch the flag style web application designed to exploit normal imperfections in the usage of cryptography. More Information: https://github.com/SpiderLabs/MCIR
Installation Of MCIR
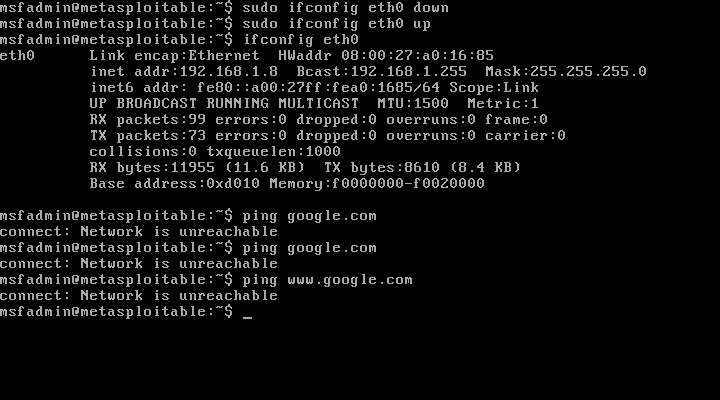
Go into Network setting in Metasploitable2 machine and put network Adapter Attached to: Bridge Adapter. Launch the Metasploitable2 machine And Run the following command to reset the network interface:
$sudo ifdown eth0
$sudo ifup eth0
Or
$sudo ifconfig eth0 down
$sudo ifconfig eth0 up
After run this command you have to give the password of user (msfadmin). Check to make sure the new IP address has been set.
$ifconfig eth0
Modify the nameservers in /etc/resolve.conf
$sudo nano /etc/resolve.conf
Set the IP Address of the name server to gateway on your network, then press Ctel+X to exit, save the file by using “y” and hit enter.
Test the Internet connectivity.
Ping www.google.com
If connectivity is established. The Next step Download the Magical Code injection Rainbow from GitHub.com.
$wget https://codeload.github.com/SpiderLab/MCIR/zip/master
The downloaded file is a ZIP container. Uncompress the master file by using following command.
$unzip master
Move the MCIR folder into Web-Server place.
$sudo mv MCIR-master /var/www/mcir
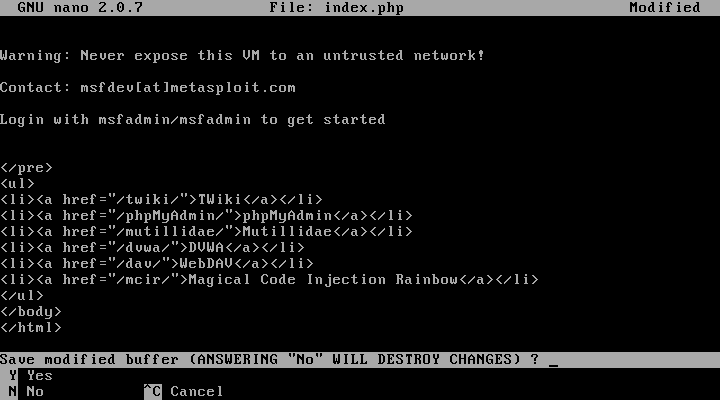
Edit the Metasploitable2 web page for access easily
$cd /var/www
$ sudo nano index.php
Add the MCIR to the list on the web page as in show in Figure.
Again go in the setting Wizerd and select Network in left menu bar then change the Attached to: Host-only Adapter. Click Ok to save changes and exit. Finally reset the network adapter card on Virtual machine of Metasploitable2.
$sudo ifdown eth0
$sudo ifup eth0
Check the IP address on the eth0 Network Interface Card.
$ifconfig eth0
Launch the Kali Linux Virtual machine, And open web browser and navigate to:
http://{IP_address_of_metasploitable2_virtual_machine}/




3 thoughts on “The Magical Code Injection Rainbow (MCIR) in Metasploitable2 Tutorial”
HI,
I am trying to do what is here, but I have some problems. There was certifications errors and it is not possible to do.
Could you help me?
The error is:
Unable to get local issuer certificate
Regards
On which steps are you getting error?
I am getting an error saying cannot establish SSL connection